[LAB1-T43] Manual Transmission
Originally posted on February 26th, 2014
Decoded by Kitt Kitt Lou (blog post)
Original TTR blog post
Old TTR Wiki page (Wayback Machine backup)
TTR Wiki's ARG blueprint archive (includes decrypted versions)
Blog post decryption method: Dvorak encoding
Encrypted |
Decrypted |
|---|---|
| :logmgr:(info) scroll time 9:31 PM TTT
:reqparser:(info) init req parsing :cryptlkr:(info) initializing encryption modules :cryptlkr:(info) got as key: SIMPLIFY BOARD :xferbse:(info) starting log transfer :xferbse:(info) using speech encryption key :lockmgr:(info) Ojabbcbi Lp.o.by >bypf Yrrb
Dmpmv Adaw f.o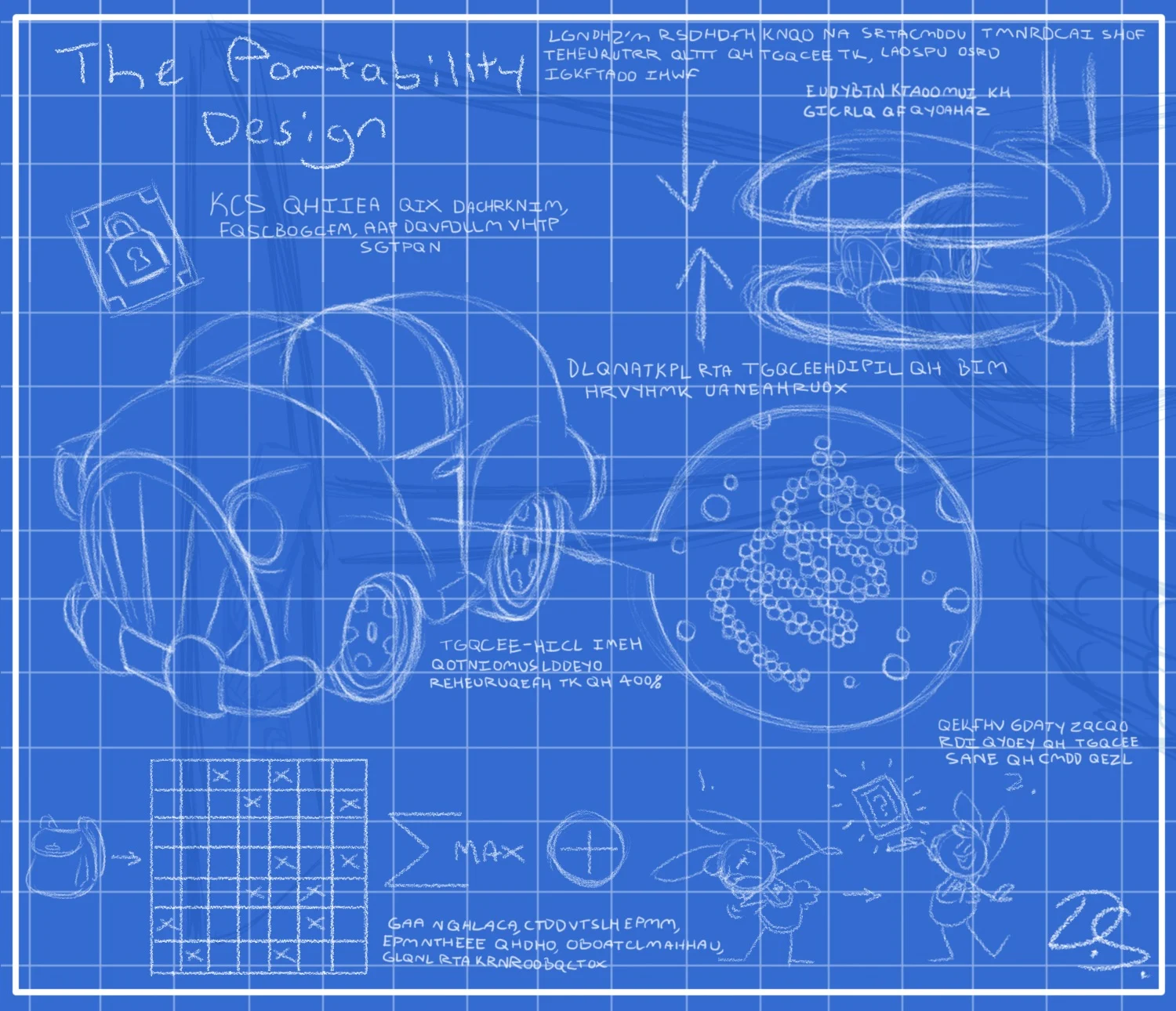 |
Blueprint decryption method:The bottom left corner of the blueprint has a 7x7 grid that correlates to the Gag menu, with several cells marked with an X. To the right of the grid is an upper case Σ (sigma), the word "MAX", and the ⊕ (circled plus) symbol. In mathematics, the sigma symbol denotes the sum of all numbers in a series - combined with "MAX", this means the sum of the max damage/healing power of the marked Gags. In XOR cipher, the circled plus symbol represents the exlusive or (also known as exclusive disjunction/alternation or logical non-equivalence/inequality) operation. Altogether, this means that the sum of the max Gag power of the marked Gags must be found, converted into binary code and put through XOR cipher using the binary code on the back of the blueprint. This is not a comprehensive summary of the decryption process - the archived TTR Wiki page at the top of this page has a more comprehensive breakdown of the decryption process. Decryption (Top to bottom, right to left):
|
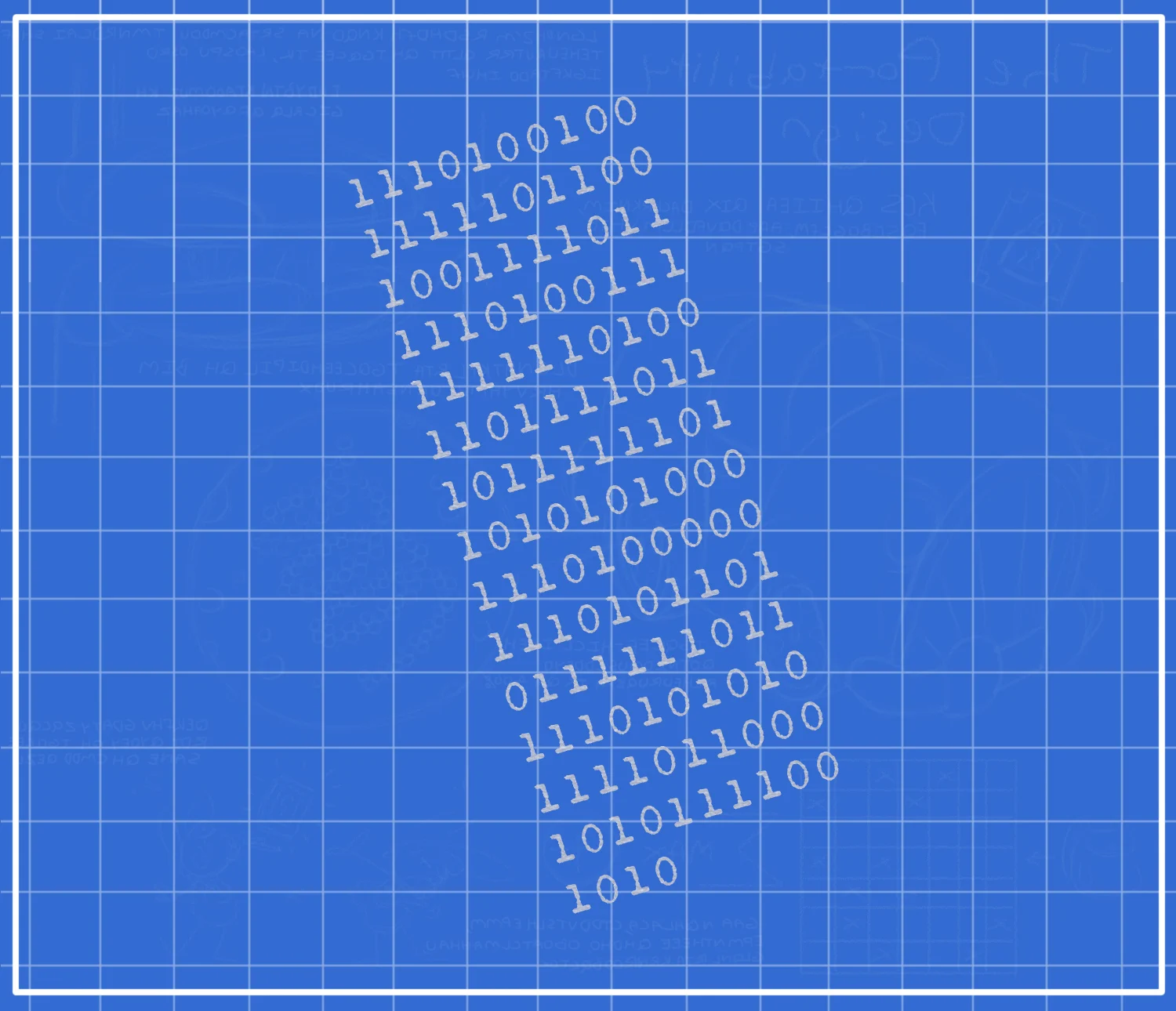 |
Decryption:
|